A Sigma and RDAP/Whois based abuse contacts finder.
This tool is highly inspired from the following libraries:
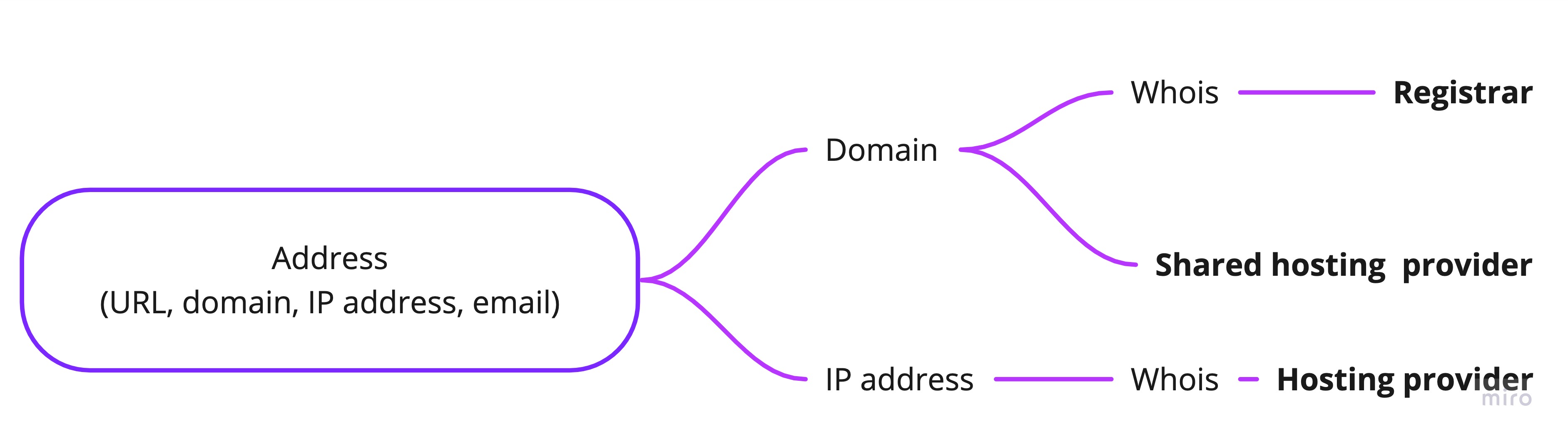
- Query a given address via RDAP (fallback to Whois is if RDAP fails)
- Check a query result with Sigma rules and find contacts (fallback to regex if there is no match)
- Python 3.10+
pip install abuse_whois
# or if you want to use built-in REST API
pip install abuse_whois[api]from abuse_whois import get_abuse_contacts
await get_abuse_contacts("1.1.1.1")
await get_abuse_contacts("github.com")
await get_abuse_contacts("https://github.com")
await get_abuse_contacts("foo@example.com")abuse_whois 1.1.1.1
abuse_whois example.com
abuse_whois foo@example.com
abuse_whois http://example.com$ uvicorn abuse_whois.api.main:app
INFO: Started server process [2283]
INFO: Waiting for application startup.
INFO: Application startup complete.
INFO: Uvicorn running on http://127.0.0.1:8000 (Press CTRL+C to quit)
$ http localhost:8000/api/whois/ address=https://github.comgit clone https://github.com/ninoseki/abuse_whois
cd abuse_whois
docker build . -t abuse-whois
docker run -i -d -p 8000:8000 abuse-whoisAll settings can be done via environment variables or .env file.
| Name | Type | Default | Desc. |
|---|---|---|---|
| QUERY_TIMEOUT | int | 10 | Timeout value for whois lookup (seconds) |
| QUERY_CACHE_SIZE | int | 1024 | Cache size for whois lookup |
| QUERY_CACHE_TTL | int | 3600 | Cache TTL value for whois lookup (seconds) |
| QUERY_MAX_RETRIES | int | 3 | Max retries on timeout error |
| ADDITIONAL_WHOIS_RULE_DIRECTORY | str | Additional contains contain whois rule files | |
| ADDITIONAL_SHARED_HOSTING_RULE_DIRECTORY | str | Additional directory contains shared hosting rule files |
abuse_whois works based on a combination of static rules and a parsing result of whois response.
Please submit a PR (or submit a feature request) if you find something missing.